2023.02.20

decentralized & verifiable IIoT product & firmware security states aka "IIoT - Security goes blockchain"
challenges
Embedded systems are used in a variety of industries, from automotive to consumer applications, and must be highly reliable due to limited computing resources. However, with increasing connectivity, the potential attack vectors of these IoT devices has grown exponentially, making them a potential threat surface. Cyber security strategies must then be implemented by manufacturers to protect these systems.challenges especially in the (I)IoT domain
Manufacturers need proof of a baseline of secure product delivery to customers, particularly in the industrial sector where products have long life cycles and are difficult to update. The EU has responded by introducing the Cyber Resilience Act (CRA) to meet common cyber security standards for networked devices and services which must be in place by September 15, 2022. This act will create the first barrier to user and customer protection.Cyber Resilience Act (CRA)
The Cyber Resilience Act (CRA) aims to implement stricter cyber security requirements for digital products on the EU market. It distinguishes a standard category for 90% of devices on the market and a critical group for the remaining 10%. This critical group is then further broken down into two classes based on criteria such as functionality, intended use, and extent of impact. To assist manufacturers in meeting these requirements, the MEDUSA SaaS tool offers an easy way to analyze, verify, and centrally store states of security based on the firmware.goals of MEDUSA
In particular, MEDUSA addresses these (I)IoT devices such as PLCs, industrial firewalls etc. – called critical "Class 2" products according to CRA. MEDUSA can analyze a certain level of status-quo security, and decentrally, verifiably re-state this condition at a later point in time.MEDUSA
ACRONYM OF MEDUSA "Multiple Emulations Dynamic Utilization System Analysis"Inspired by plain firmware emulation, MEDUSA has been created as SaaS solution to develope, evaluate and pentest own or other products for functionality without hardware in a comfortable and automated environment. Download your tailored firmware image or let it run on the provided infrastructure and connect via VPN.
MEDUSA combines the power of open source emulation tools, established build systems and custom technology to form an embedded device emulation system based on Linux, Android, Harmony OS and other proprietary platforms.
With this comes numerous use cases for different domains such as OT, IoT and all other types of embedded devices. MEDUSA thus enables accelerated and simplified development, functional (test automation) through to cyber security testing or support in research.
In addition to the executable "digital twin" that re-hosts physical devices as SaaS or local instance, MEDUSA also provides a static vulnerability analysis of the status quo from the vulnerability point of view. With this, known vulnerabilities in a firmware can be determined according to the CVE numbers.
context & how we use blockchain
CyberDanube has chosen to integrate a trust authority, ITD, into their software, offering a simple implementation via their API. They store a hash value in the blockchain which is based on the firmware, analysis results and entropy. The authentication process is automated with no further user interaction, and users can verify its correctness with the latest time stamp (marked in red) in the screenshot as "Minted".
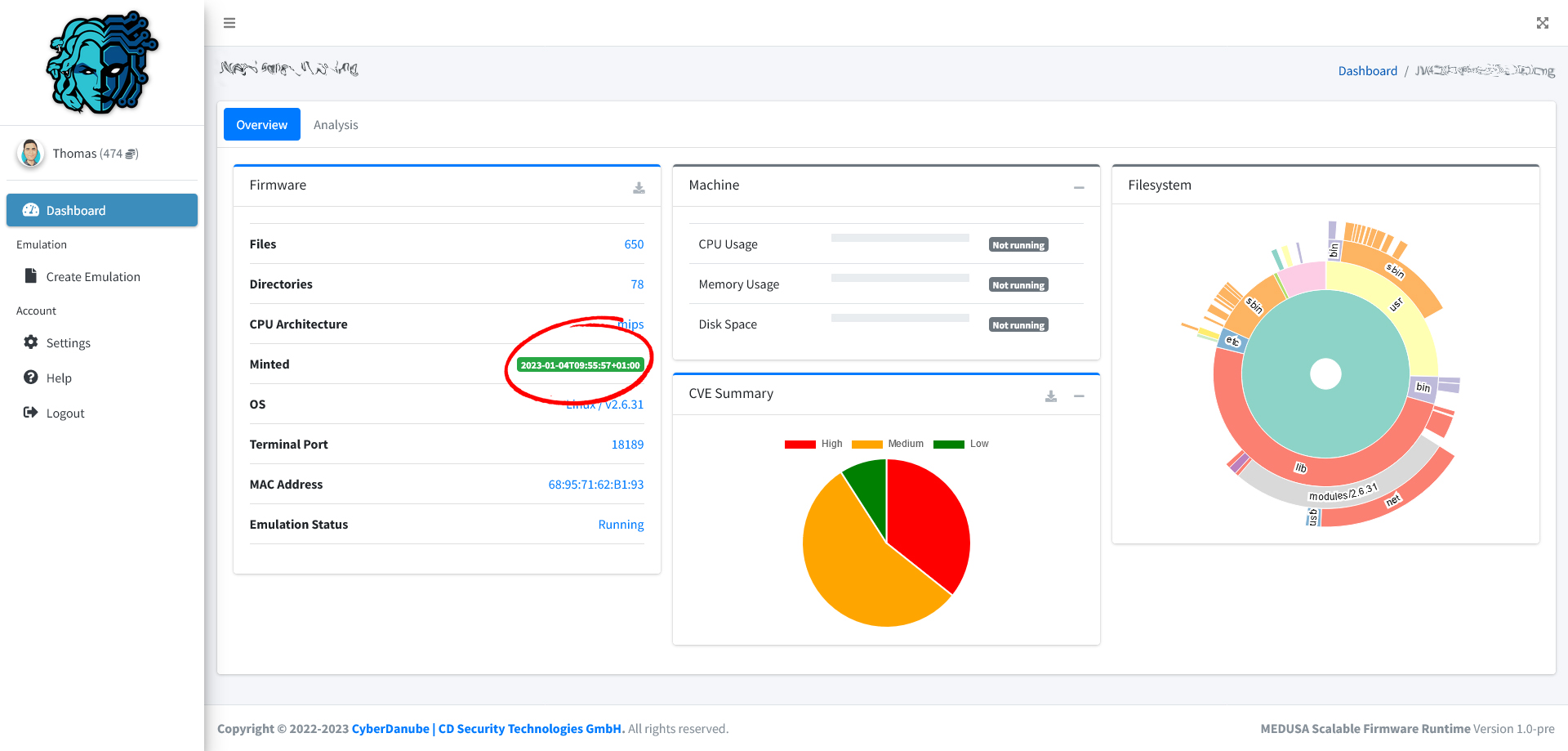
conclusion
infinite trust digital GmbH offers a blockchain solution which is based on a DACH consortium and a "proof of authority" in a "round robin principle" approach. This solution fits the needs of the technology strategy perfectly and is in line with the "made in Austria" concept. With this technology, customers can benefit from advanced technology and transparency in their business processes and in terms of (I)IoT and product security.Contact: Mario-Valentin Trompeter to a live demo & showcase // cyberdanube.com office@cyberdanube.com
For more information on Blockchain tech and how to implement Blockchain applications in a real world scenario do not hesitate to contact us at office@infinite-trust-digital.com
@Copyright 2023 - Infinite Trust Digital GmbH
